Keycloak SSO offers a practical path for modernizing legacy systems without starting from scratch. By centralizing authentication and enabling flexible login options, it simplifies user management, strengthens security, and allows organizations to adopt modern identity standards while keeping their existing infrastructure intact.
Keycloak SSO: Bridging Legacy Systems and Modern Identity Management
I believe everyone who’s in IT longer than couple of earth rotations around the sun has faced similar challenge: „We have something old, we want something new and both should work at the same time flawlessly“. This is especially challenging when dealing with front facing services which secure access to your environment. Usually customer wants to implement some modern protocol for authentication/authorization to allow for better security, usability and reach but the legacy backend app is on the opposite side of the idea (otherwise it would not earn „legacy“ adjective).
Why Keycloak Is Ideal for Legacy IAM Integration
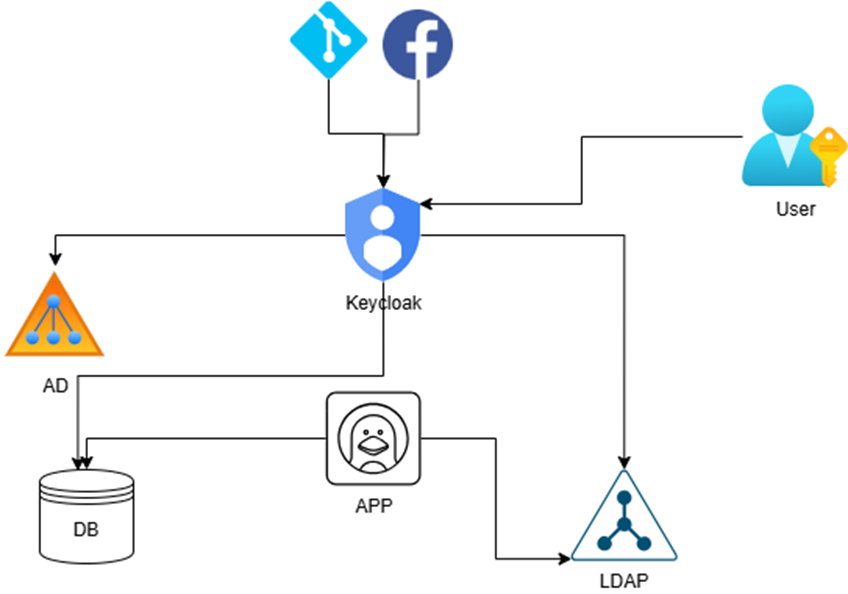
One of the common tools used for bridging that gap is known by the name „Keycloak“.
Smart folks from RedHat and Open Source community thought about it and allowed everyone with a bit of coding skills to extend the nature of this authentication and authorization service.
All comes down to getting to know some basic elements of Service Provider Interfaces and you can create your own custom Authenticator which can bridge the gap between legacy and modern. So, back to our use case…Let’s imagine we want to implement „Login with Facebook, Google, Git…“ feature on something that existed before 4th of September 1998. Or even better, we don’t want our users to use a password at all when authenticating to legacy app. Don’t get us started on all the benefits of SSO approach there.
Keycloak SSO Setup for Legacy Applications
You could go with something like this:
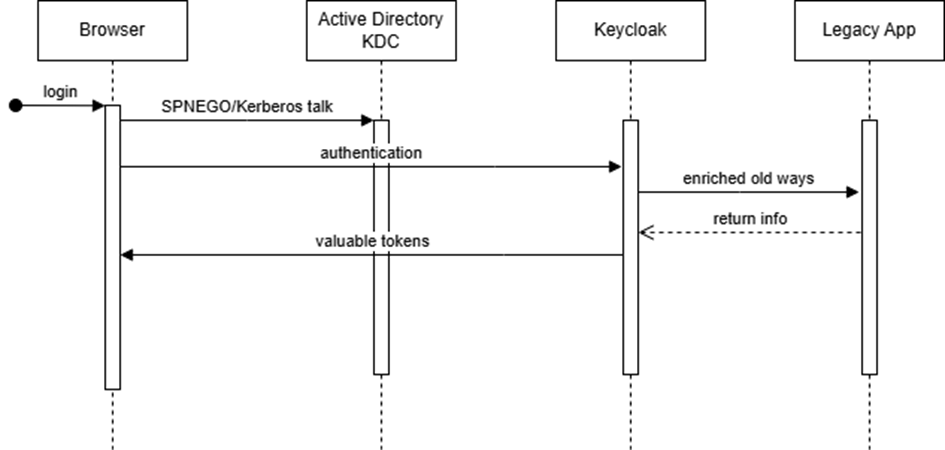
When a user clicks on the app, it is redirected to Keycloak login page. Now there are two possible scenarios (there could be more, but for the sake of readers we will limit our selves to just these two):
- Users browser talks with KDC/AD and authenticates the user without the need for username/password input
- Otherwise user can login using classic username/password/2FA or utilize some social login option mentioned earlier
In both cases, Keycloak will talk with legacy app and make sure the app gets all the info it needs to allow user access (calling an old SOAP service or legacy DB). At the same time customized authentication flow will generate all standard tokens if we are talking about OIDC/OAuth2.0 which can be utilized further down the road.
What we did here we allowed interaction between legacy app, utilized relevant data, included cool features from modern IAM tool and delivered seamless experience to our customers. Now the customer has space to gradually move their user base and work on modernization of existing infrastructure.
For a hands-on example of how Keycloak was implemented in a real-world student engineering project, check out this blog from the CROZ Summer Accelerator.
Conclusion
Using Keycloak as a bridge between old and new IAM worlds enables a smoother transition to modern standards without disrupting existing systems. Whether you need SSO, OAuth2, passwordless login, or social authentication, Keycloak provides a robust set of tools to connect your legacy application to today’s identity stack. With features like customizable authentication flows, protocol mappers, and support for legacy identity providers, Keycloak SSO makes it possible to unify fragmented access control into a single, cohesive experience. This approach not only enhances security and user convenience, but also reduces development overhead when modernizing complex environments. By gradually integrating Keycloak SSO into legacy systems, organizations can modernize at their own pace while keeping operations stable and secure.