Right off the bat, I’ll ask you to take a moment and think about your password. You know the one. The one password you reuse on all your personal accounts. If you’re a bit more security-conscious you’ll rotate your passwords, use different ones for different accounts and all that jazz.
So now you hit a point where you must remember a whole bunch of strong passwords, maybe you’ll use the XKCD system of mnemonics or, much more likely, you’ll opt for a password manager such as LastPass or KeePass. That’s fine. Those are good tools. But they don’t protect you from password leaks or lucky guesses, so now you have to find some extra layer of protection.
As you’ve probably guessed, this is where two-factor authentication comes into play. The common suspects here are Google Auth and FreeOTP. As you may have heard, there has recently been malware that steals 2FA codes from Android devices. Breach of security, of course, is a thing that happens to other people, so we’re safe for now in our land of hypotheticals.
Now that the stage is set the first thing that could be inferred is that all this is a lot of hassle. Rotating your logins, taking care of 2FA codes, not losing access to them, having a backup of your KeePass database, etc. is a bit of a chore. Therefore, there’s an ongoing move to use more “modern” authentication methods, and the most prominent and buzzwordy one is going passwordless. Chances are you’ve been using this method for a while now and didn’t even think about it.
Going Passwordless
Using your fingerprint for unlocking your smartphone? Using your ID card to log in to government services? Maybe you have a YubiKey, or your office enforces the use of SmartCard logins on your PC? These are all passwordless solutions that are already widely used.
What passwordless authentication really allows you is to use something only you have access to but isn’t based on knowledge. Examples would be your fingerprints, face, smartphone, key tokens, and smart cards, and if you enjoy spy movies, your retina and voice imprints. They are all unique things that cannot be copied just like that. It’s really similar to how a conventional door key works.
Along with the passwordless world, there’s a surge in multi-factor authentication often combined with other authentication methods to provide maximum security. This implies providing credentials from multiple unrelated sources, such as one-time passwords you can receive via SMS or OTP apps and your passwords or passwordless credentials. The world of cyber security is vast and interesting indeed.
Another thing that ties really well into passwordless is single sign-on (SSO) type authentication. SSO is a way to use a single account to access all resources within an organization. A real-life example of this would be those endless “Sign in with Google/Facebook/X” prompts you to see on almost every web page now. You simply log into Google, and they confirm your identity to all other services without showing them your credentials. Passwordless mechanisms are pretty varied and easy to adapt to your needs. You can use the account you logged into Windows with, a smart card, your smartphone, biometrics, hardware keys, and many more fun toys.
Keycloak
All this and much more are available for use in one of our favorite pieces of software here in the Systems room, and that is, of course, Keycloak. This FOSS identity and access management tool is the upstream version of Red Hat SSO much like Fedora is to their RHEL OS. Boasting support for OpenID Connect, SAML, and OAuth 2.0, it provides SSO support to anything you could ever want to connect to it. It offers you the ability to get your users from practically any user directory, be it LDAP, AD, or Kerberos, while also supporting social providers like Google and Facebook. Your login page can be fully customized to suit your needs and to keep stuff nice and safe. It also offers you passwordless authentication via all those cool things I’ve covered earlier, MFA, and any number of custom login flows.
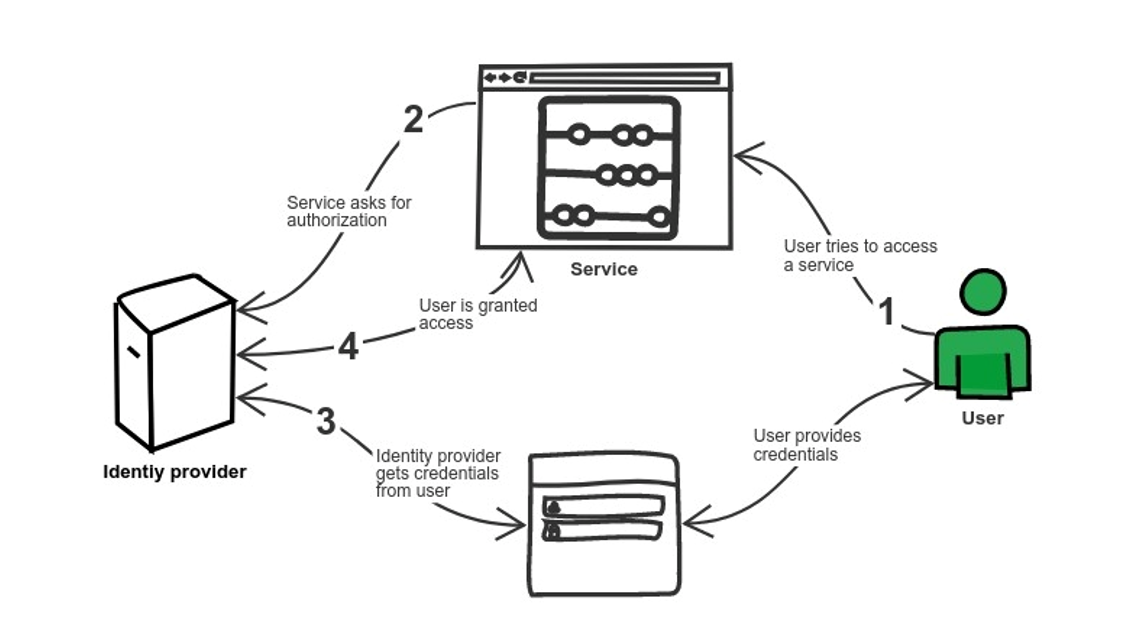
Simple example of an SSO login flow
Another cool thing is that you’re not limited to a single platform with Keycloak being able to run in any environment, be it a K8S cluster, a Docker image you’ve deployed just for fun, or a dedicated virtual machine. Any way you run it, the functionality is the same, giving your admins the ability to control every last detail of the authentication process and fully audit it. As a community-driven piece of software, it’s always being updated, and the speed between finding a critical flaw and a fix coming out can be incredibly fast.
With all these lovely features, we couldn’t help but set it up as our preferred internal SSO provider here at CROZ. It has also become a major part of the security architecture for our AI platform, securing all user-facing components – and that is something we will, for sure, talk about more later on.
In the end, there are plenty of SSO providers out there, but over the years, Keycloak has proved itself as one of the most reliable and versatile tools we tried out. Thus, both us and our clients plan to keep on using it for the foreseeable future.

