Introduction
In today’s data-driven world, organizations face the challenge of Data Governance across multiple platforms: cloud, hybrid, and on-premise infrastructures. With the rising volume of data, the complexity of metadata management grows, requiring robust solutions for ensuring data reliability, accountability, and transparency.
The shift towards Data-as-a-Product (DaaP) means embracing a decentralized, self-service approach to data management. But how can organizations ensure that metadata remains secure, scalable, and accessible across all environments? How do AI and machine learning impact metadata governance, adding another layer of complexity?
Here at CROZ, our Data Governance Assessment Service helps align governance strategies with your business objectives, unlocking the full potential of your data.
Our Approach
We’ve developed a comprehensive Data Governance Tool assessment service that helps you manage metadata with precision. Our structured approach includes:
- Initial Consultation
- Data Catalog Assessment
- Business Requirement Mapping
- Gap Analysis
- Custom Recommendations & Implementation Plan
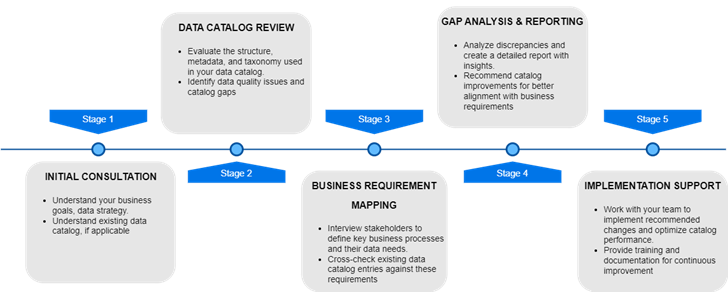
Step-by-Step Process: How do we help
Step 1: Initial Consultation
We start by gaining a clear understanding of your business goals and your current approach to metadata management. Through a detailed workshop, we discuss key challenges and your existing processes.
- What are the specific challenges with metadata security and access control?
- How is metadata currently organized and managed within your system?
- Do you have regulations or internal policies (e.g., GDPR) concerning metadata privacy?
Step 2: Data Catalog Review
After we understand your needs, we review your existing data catalog and metadata practices. This helps us identify gaps in areas like role-based access control (RBAC), audit trails, and encryption.
- Identify gaps in metadata security and access control.
- Review existing audit trails and logging mechanisms.
- Ensure encryption for sensitive metadata fields.
Step 3: Business Requirement Mapping
We work with your stakeholders to map business processes to your metadata needs. This step ensures that critical data assets are easily accessible and organized for business use cases.
- Map role-based access needs to specific metadata assets.
- Define granular access controls for different user roles.
- Identify key metadata that needs to be highlighted for easy search and discovery.
Step 4: Gap Analysis & Reporting
Following our business requirement mapping, we conduct a thorough gap analysis to uncover discrepancies between your current data practices and your objectives. Our report will include:
- Security gaps, such as insufficient audit trails or weak encryption.
- Opportunities for improving metadata searchability and organization.
- Actionable recommendations for better metadata management.
Step 5: Implementation Support
Once we’ve identified the necessary improvements, we assist in implementing the changes. This includes setting up role-based access control (RBAC), encryption protocols, audit trail mechanisms, and organizing metadata for better accessibility.
- Enforce role-based access controls and data security protocols.
- Implement encryption for sensitive data.
- Organize metadata to improve data discovery.
- Provide training and documentation to ensure continuous improvement.
Example: How Our Process Works in Action
Here’s an example of how we helped a client improve their data governance process:
A client approached us with a clear request:
“We need a data governance solution that ensures our metadata remains secure and accessible only to authorized users. We are focused on implementing strong privacy and access controls for metadata and improving data discovery for key business use cases.”
Our five-step assessment process included:
- Initial Scanning: We hosted a workshop to understand their challenges with metadata security, access control, and organization.
- Data Catalog Review: Our analysis revealed gaps in RBAC and encryption, as well as inefficiencies in metadata organization.
- Business Requirement Mapping: We defined clear access levels and identified critical metadata for improved discovery.
- Gap Analysis: We identified several security gaps and opportunities to streamline metadata searchability.
- Implementation: We helped implement role-based controls, encryption protocols, and reorganized metadata to improve search and accessibility.
But why CROZ?
Our team has extensive experience in data governance, business analysis, and IT solutions. We tailor our approach to your unique needs, ensuring that metadata management aligns with your business goals. We offer end-to-end support from assessment to implementation, helping you secure and optimize your data.
Let’s get started!
If you’re ready to take your data management to the next level, contact CROZ for a free consultation. Read our flyer to find out more.


